Defend Against DNS Flooding Attacks with Nexusguard’s DNSShield

Nexusguard

Share to:
In an era where DNS attacks are growing in complexity, Nexusguard’s DNSShield offers a powerful solution to protect your domain infrastructure. Designed to address stealthy Layer 7 domain-level flooding attacks — such as NXDomain and Phantom Domain attacks — DNSShield integrates seamlessly into Nexusguard’s reverse proxy framework. It provides continuous, proactive mitigation without relying on detection or alerts, ensuring your DNS services stay resilient and responsive. Tailored to safeguard authorized name servers and DNS resolvers, DNSShield leverages advanced filter rules to deliver robust, always-on protection.
How to Set Up DNSShield
DNSShield offers a flexible and intuitive setup process, allowing you to configure protection on a per-site or per-name-server basis. This granular control ensures that you can tailor DNSShield’s defenses to meet the specific needs of your infrastructure.
DNSShield includes an independent ON/OFF switch for each profile, giving you complete control over when and where the protection is applied. This feature is especially useful for testing, troubleshooting, or gradually rolling out DNSShield across multiple sites or servers.
DNSShield is designed to work in harmony with Nexusguard’s NetShield and L3-4 mitigation services. Once NetShield has handled lower-layer (L3-4) threats, DNSShield executes its advanced DNS-specific protections, ensuring a comprehensive defense strategy that covers all layers of the OSI model.
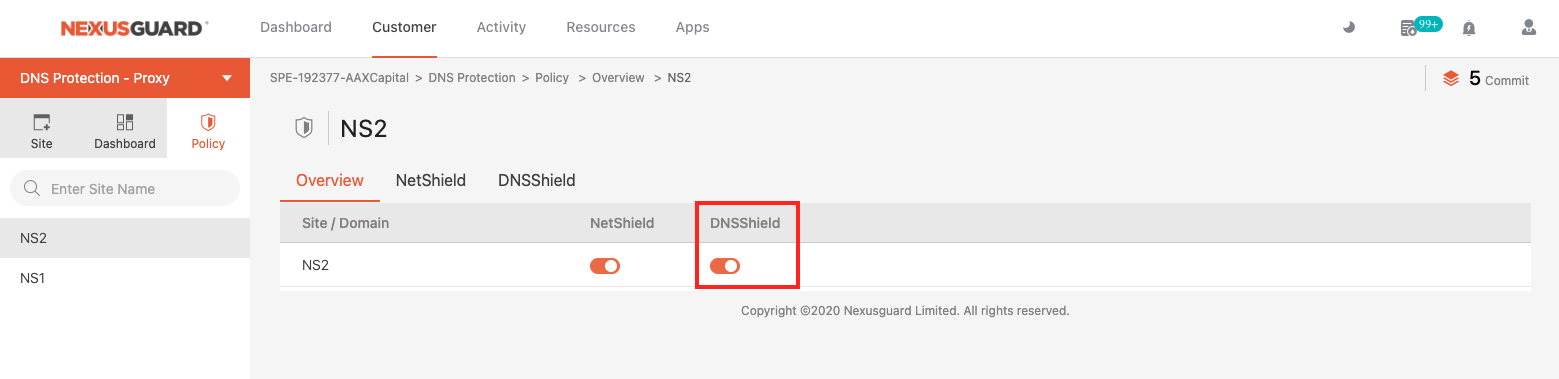
How DNSShield Works
DNSShield employs three powerful countermeasures to enhance DNS protection:
- Domain Filter – Implements zone-level allowlists and blocklists to control access to specific domains.
- NXDomain Filter – Monitors and regulates the query rate for non-existent zones, preventing overload from invalid requests.
- DNS Error Cache – Stores DNS error responses for recurring queries, reducing redundant processing and improving efficiency.
Domain Filter
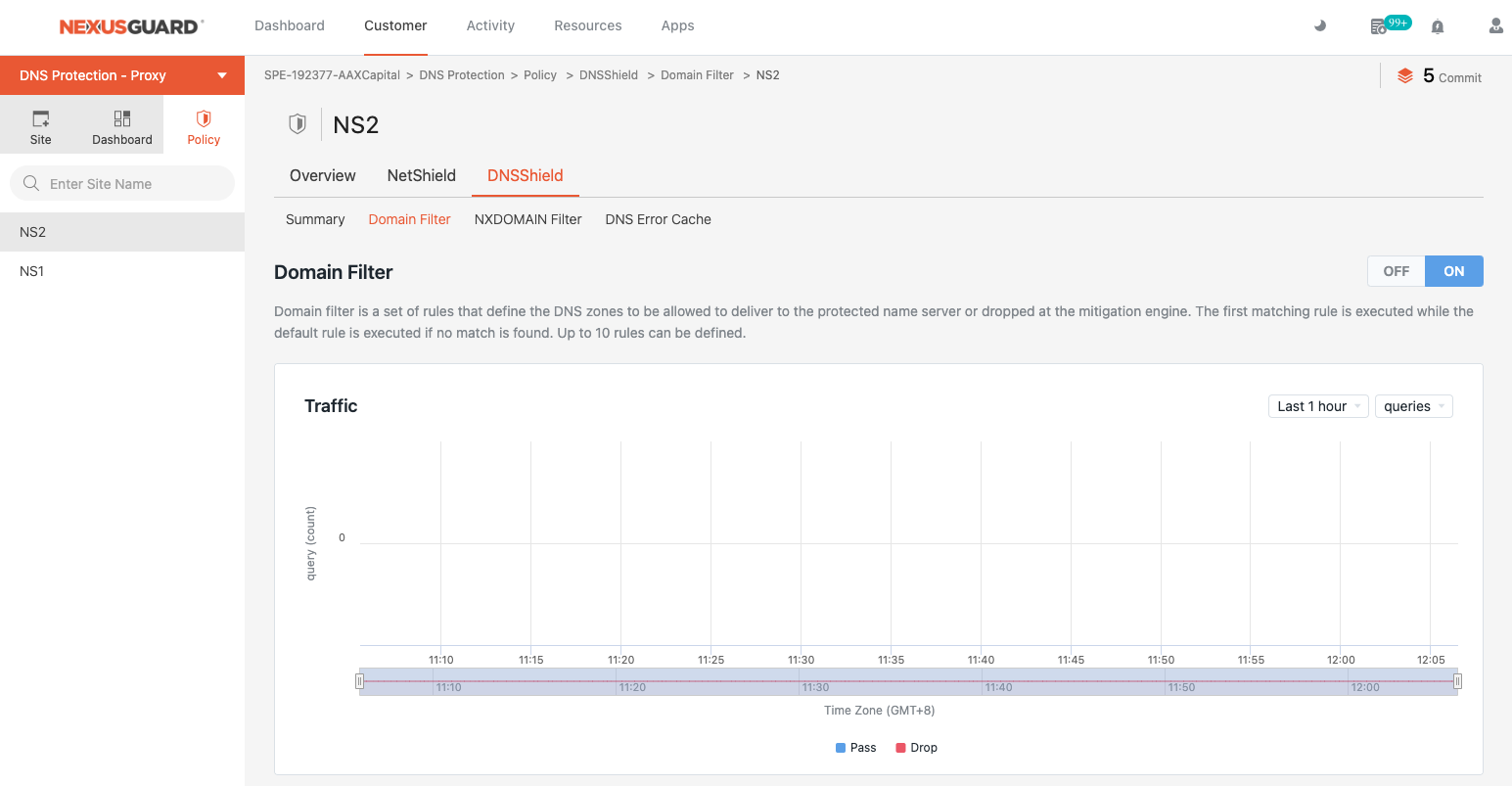
Domain Filter includes several customizable filter rules, with the default_rule always executing last. The default_rule serves as the final checkpoint, ensuring comprehensive filtering after all other rules have been applied.
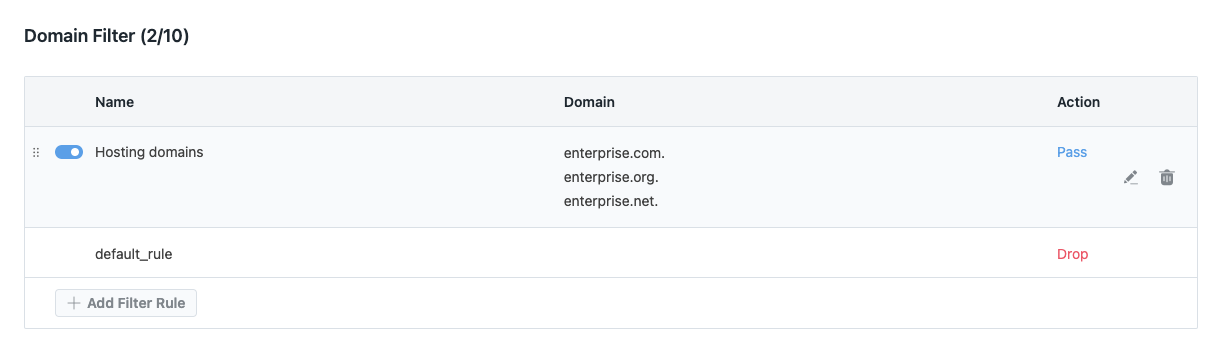
Domain Filter is designed to safeguard authorized name servers by allowing or blocking queries based on predefined zones. This feature is particularly effective when you have a clear understanding of the specific zones that should be permitted or denied. By default, the Domain Filter is set to Drop, ensuring that any queries not explicitly allowed by prior rules are automatically blocked.
NXDomain Filter
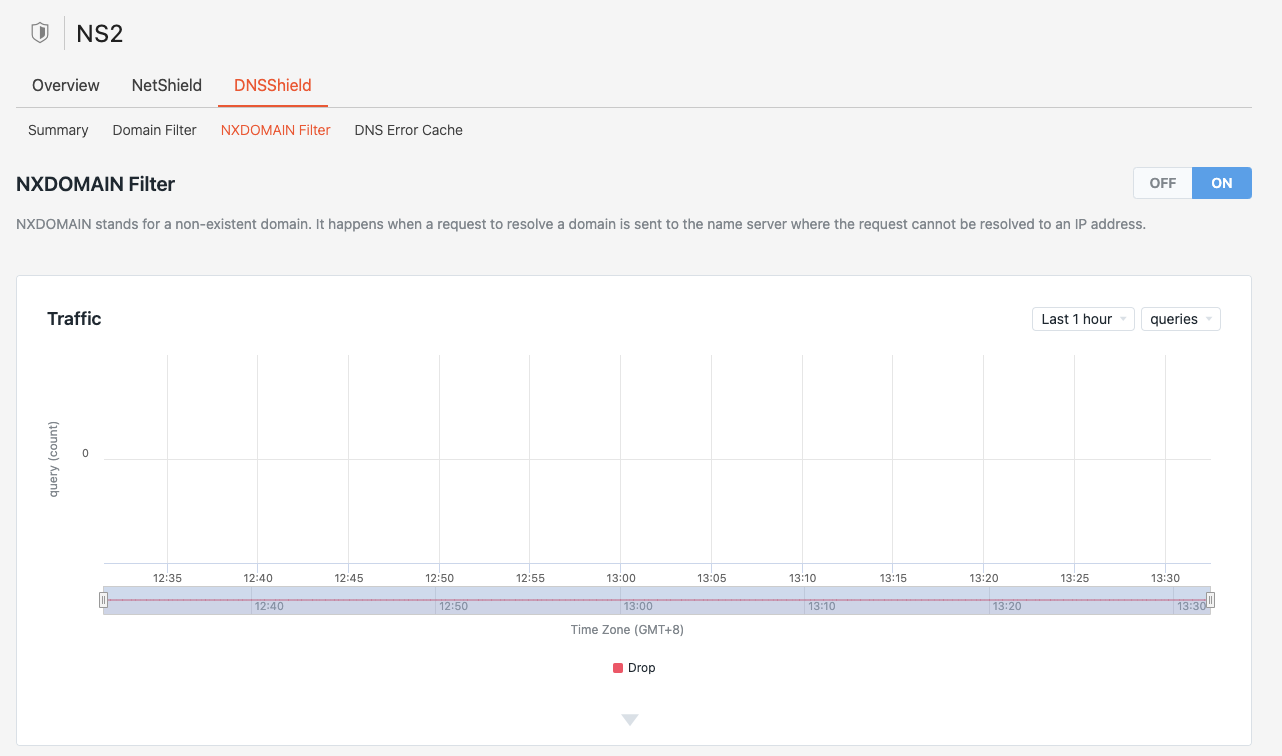
NXDomain Filter is activated after the Domain Filter to inspect and mitigate traffic that has passed through the initial filtering stage. This ensures an additional layer of protection by targeting and regulating invalid queries for non-existent domains.
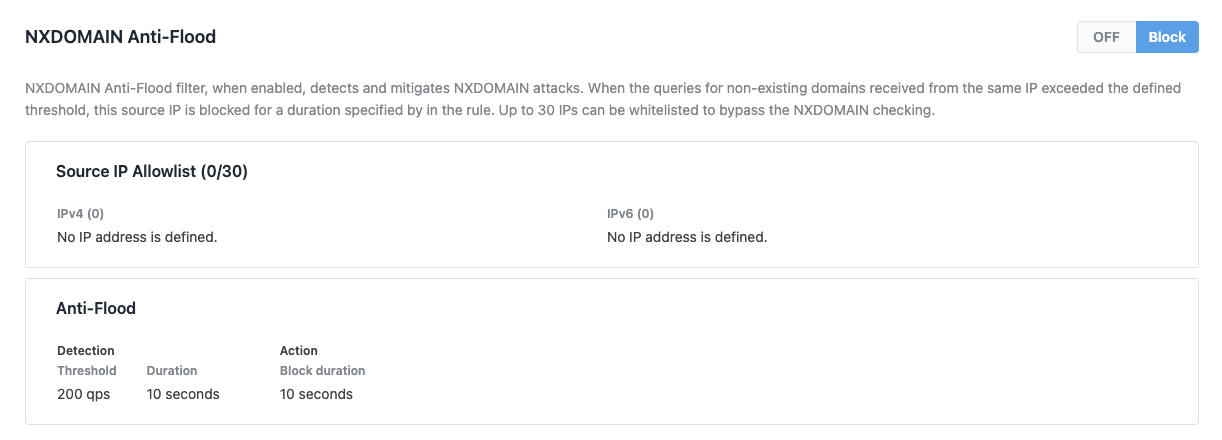
NXDomain filter tracks the number of NXDomain queries originating from each source IP. If a source IP exceeds the predefined threshold, the filter blocks all DNS requests from that IP for a specified duration. Once the blocking period ends, the source IP is allowed to resume queries, provided it stays within the acceptable rate limit.
DNS Error Cache
DNS Error Cache is a smart caching mechanism designed to handle repetitive queries for invalid or non-existent domains more efficiently. While it’s not a filter in the traditional sense, it plays a critical role in enhancing your DNS server’s performance and resilience.

Key Features
- 3 Pre-Defined Lifetimes
The DNS Error Cache operates with three pre-defined caching durations, allowing you to balance performance and resource efficiency. These lifetimes determine how long error responses (e.g., NXDomain, SERVFAIL) are stored before being refreshed, ensuring optimal handling of repetitive invalid queries.
- Caches DNS Return Codes Other Than NOERROR
The cache specifically stores DNS error responses, such as NXDomain (non-existent domain) or SERVFAIL (server failure), while excluding successful responses (NOERROR). This targeted approach ensures that only problematic queries are optimized, leaving legitimate traffic unaffected.
- Absorbs Large Volumes of Invalid DNS Requests
By caching error responses, the DNS Error Cache effectively absorbs and neutralizes massive volumes of invalid queries. This reduces the load on your DNS servers and upstream infrastructure, preventing resource exhaustion and maintaining service availability.
- Applicable in All Situations as a Last Line of Defense
DNS Error Cache operates as the final safeguard in your DNS query processing chain. After all other filters and rules have been applied, this caching mechanism steps in to manage repetitive queries for non-existent or invalid domains, ensuring comprehensive protection across all scenarios.
Protection Policy for Authoritative Name Servers
When your authoritative name server is under protection, it’s essential to implement a robust defense strategy tailored to the specific zones it hosts. Since the server manages a well-defined list of zones, you can leverage DNSShield’s features to create a highly effective protection policy.
Suggested Protection Policy:
- Domain Filter: Allowlist Hosting Zones
Action: Add all hosted zones to the allowlist.
Result: Queries for domains within these zones are permitted, while requests for any other zones are automatically dropped.
- NXDOMAIN Filter: Regulate Invalid Subdomain Queries
Action: Enable the NXDOMAIN filter to monitor and control queries for non-existent or invalid subdomains within your hosted zones.
Result: The filter regulates the rate of such queries, preventing attackers from overwhelming your server with repetitive requests for fake subdomains.
- DNS Error Cache: Absorb All Other Invalid Queries
Action: Enable the DNS Error Cache to handle and cache error responses for invalid queries that slip through the first two layers of defense.
Result: Repetitive invalid queries are absorbed locally, reducing the load on your server and upstream infrastructure.
Protection Policy for Recursive Resolvers
When the name server under protection is operating as a recursive resolver, it must handle DNS queries for any zone, making it a prime target for a wide range of attacks. To safeguard your resolver, DNSShield offers a multi-layered defense strategy tailored to this dynamic environment.
Suggested Protection Policy:
- Domain Filter: Block Known Invalid Zones
Action: Use the Domain Filter to drop queries for known invalid or malicious zones identified during attacks.
Result: This immediately blocks traffic to harmful or non-legitimate domains, reducing the attack surface and conserving server resources.
- NXDomain Filter: Regulate Queries for Non-Existent Zones
Action: Enable the NXDomain Filter to control the rate of queries for non-existent or invalid zones.
Result: The filter throttles or blocks excessive queries for domains that don’t exist, preventing attackers from overwhelming your resolver with fake requests.
- DNS Error Cache: Absorb All Other Invalid Queries
Action: Enable the DNS Error Cache to handle and cache error responses for any remaining invalid queries.
Result: Repetitive invalid queries are absorbed locally, reducing the load on your resolver and upstream infrastructure.
Establish your cybersecurity defense strategy today to fortify your authoritative name servers and recursive resolvers using Nexusguard's DNSShield. Contact one of our experts now to get started.
Protect Your Infrastructure Today
.avif)











